
At least 25,000 iOS apps available in Apple's App Store contain a critical vulnerability that may completely cripple HTTPS protections designed to prevent man-in-the-middle attacks that steal or modify sensitive data, security researchers warned.
As was the case with a separate HTTPS vulnerability reported earlier this week that affected 1,500 iOS apps, the bug resides in AFNetworking, an open-source code library that allows developers to drop networking capabilities into their iOS and OS X apps. Any app that uses a version of AFNetworking prior to the just-released 2.5.3 may expose data that's trivial for hackers to monitor or modify, even when it's protected by the secure sockets layer (SSL) protocol. The vulnerability can be exploited by using any valid SSL certificate for any domain name, as long as the digital credential was issued by a browser-trusted certificate authority (CA)."The result is an attacker with any valid certificate can eavesdrop on or modify an SSL session initiated by an app with this flawed library," Nate Lawson, the founder of security analytics startup SourceDNA, told Ars. "The flaw is that the domain name is not checked in the cert, even though the cert is checked to be sure it was issued by a valid CA. For example, I can pretend to be 'microsoft.com' just by presenting a valid cert for 'sourcedna.com.'"
Lawson estimated that the number of affected iOS apps ranged from 25,000 to as high as 50,000. SourceDNA has provided a free search tool that end users and developers can query to see if their apps are vulnerable. To make it harder for attackers to exploit the vulnerability maliciously, SourceDNA isn't providing a comprehensive list of vulnerable apps.
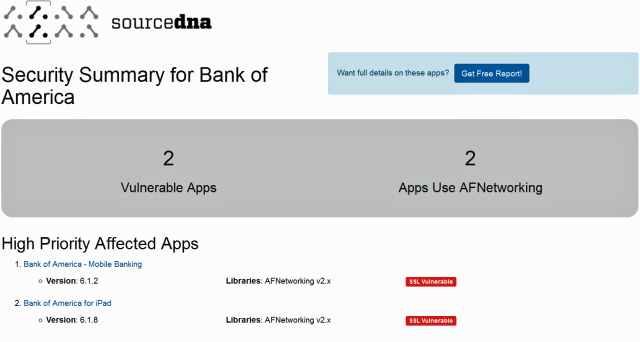
A quick check found that apps from Bank of America, Wells Fargo, and JPMorgan Chase were likely affected, although some of those reports may be false positives. It's possible that some apps flagged by SourceDNA use custom code or secondary measures such as certificate pinning that prevents attacks from working. Apps from Microsoft, meanwhile, remained vulnerable to the HTTPS-crippling bug reported earlier.
Game over
The new vulnerability is the result of a bug in AFNetworking that fails to ensure the domain name contained in the certificate matches the domain name of the HTTPS server it protects. As a result, anyone with a man-in-the-middle position—say, an attacker on an unsecured Wi-Fi hotspot, a rogue employee inside an Internet service or virtual private network provider, or a state-sponsored hacker sniffing the Internet backbone—can present their own CA-issued certificate, then read or tamper with the protected communications.
Unlike the AFNetworking vulnerability Ars reported Monday, this newly reported bug is present in all 2.x versions of the code library except the latest version 2.5.3.
As if it wasn't enough that at least 25,000 apps have been vulnerable to such a simple attack for so long, there's another glaring oversight involved. AFNetworking maintainers actually had updated code fixing the bug at the end of March, around the same time that the previous flaw was fixed. The so-called commit, however, was never included in the version 2.5.2 release.
SourceDNA credited Ivan Leichtling with being the first person to report the flaw. An AFNetworking developer released 2.5.3 the next business day after SourceDNA notified him that the crucial commit was missing from 2.5.2, but he never replied to the SourceDNA e-mail, Lawson said.
In a blog post published Friday morning, SourceDNA researchers wrote:
We notified our customers and contacted the developer. He released the updated version 2.5.3 earlier this week. If you are using AFNetworking (any version), you must upgrade to 2.5.3. Also, you should enable public key or certificate-based pinning as an extra defense. Neither of these game-over SSL bugs affected apps using pinning.
This also shows that a bug is not truly fixed until it has made it into a release and into your apps and out to the app stores. Developers need to track the code in their apps to be sure patches aren't lost along the way. Our Searchlight service can help you do just that, giving you immediate info on flaws that affect your apps.
We've updated Searchlight to show which apps are still vulnerable, and we'll continue to publish new results there as affected apps are updated. If you're an iOS developer, please sign up now to get notices when SourceDNA finds security issues that affect your apps.
iOS users should immediately check the status of any apps they use, especially if the apps convey bank account numbers or other sensitive personal information. It may take the developers of vulnerable apps a few days to release an update that incorporates the AFNetworking fix, so users should be prepared to avoid any vulnerable versions for the time being. The AFNetworking error affects only apps that use the code library. The device itself and other apps, including browsers, aren't affected by the flaw, even if one or more apps on the device are vulnerable.
reader comments
89