Malaysian authorities announced today they had identified the possible authors of a massive data breach that took place a month ago and during which the personal details of 46.2 million Malaysians were put up for sale on the Dark Web and various forums.
The breach came to light at the end of October when an anonymous user alerted Lowyat.net, a Kuala Lumpur-based technology site, about data belonging to millions of Malaysians being sold online on the Dark Web.
After news broke of the incident, the data became a must-have for all hackers and quickly spread as a free download on a variety of underground hacking forums.
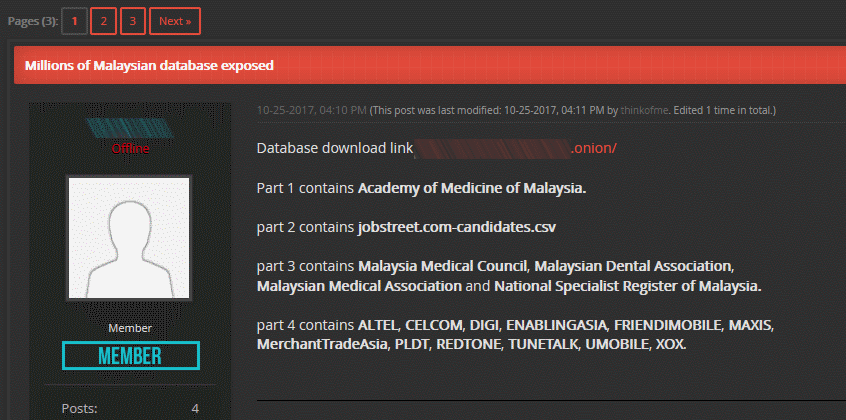
The stolen data contained information on 46.2 million mobile numbers from almost all of Malaysia telephony providers, including Altel, Celcom, DiGi, Enabling Asia, Friendimobile, Maxis, MerchantTradeAsia, PLDT, RedTone, TuneTalk, Umobile, and XOX.
Included in the shared files were telephone numbers and names for each subscriber, and highly sensitive details such as identity card numbers, home addresses, IMSI, IMEI, and SIM numbers.
The data also contained private details for more than 80,000 individuals from records stolen from the Malaysian Medical Council, the Malaysian Medical Association, and the Malaysian Dental Association. All stolen data appears to have been stolen no later than July 2014.
Police says they're getting closer to arresting the culprits
In a press conference today, Inspector-General of Police Tan Sri Mohamad Fuzi Harun said investigators have pinpointed the possible culprits, which they believe to be the employees of a company that was involved with the transfer of the stolen data.
Mohamad Fuzi did not detail what kind of transfer took place, nor how many people they suspect to be involved, but said the fault does not appear to be with any of the telcos.
Malaysian police have not made any arrests at the time of writing.
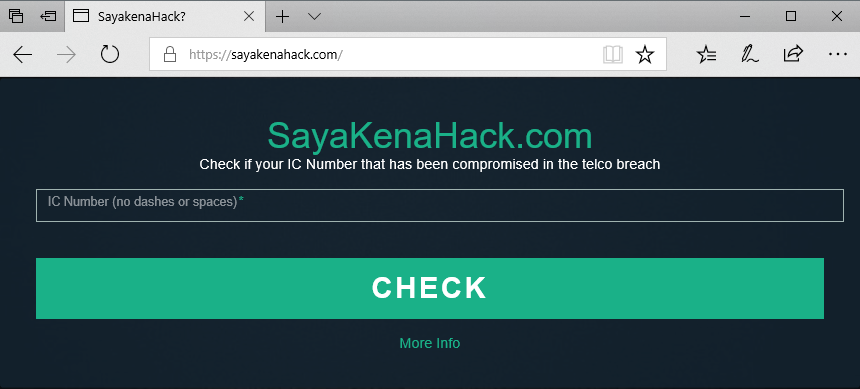
Instead, another state agency —the Data Privacy Protection Department (JPDP)— intervened and blocked a website set up by Malaysian security researcher Keith Rozaria that allowed victims to search and see if they were included in the leaked data.
The site —located at SayaKenaHack.com— was blocked locally. Rozaria responded by setting up a mirror to bypass ISP filters.
This is not the first hack to affect an entire country. Similar mega-breaches have also taken place in the Philippines (55 million), Turkey (50 million), and South Africa (30 million). Off all incidents, police have only arrested the hacktivists behind the Philippines breach.
.jpg)

Comments
trickytophat - 6 years ago
Wow, the details of 46.2 Malaysians... How many million is that?