F-Secure’s Attack Landscape Report for H1 2019 Paints a Pretty Grim Picture
- F-Secure’s Attack Landscape Report paints a dire picture of today's global cybersecurity state.
- The number of attack events has gone three times up compared to the previous six-month period.
- IoT devices seem to take the lion’s share in the attention of cybercrooks, with over 760 million attacks.
The renowned Finish cybersecurity and privacy expert F-Secure, has compiled data from its honeypots and published a report that defines the attack landscape for the first half of 2019. As expected, the situation is much worse than it was a year ago for the same period, as the total number of attacks measured surpassed 2.9 billion. This is about three times higher than H2 2018, 12.5 times higher when compared to H1 2018, and the very first time that the number of attack events exceeded the billion mark.
Source: f-secure.com
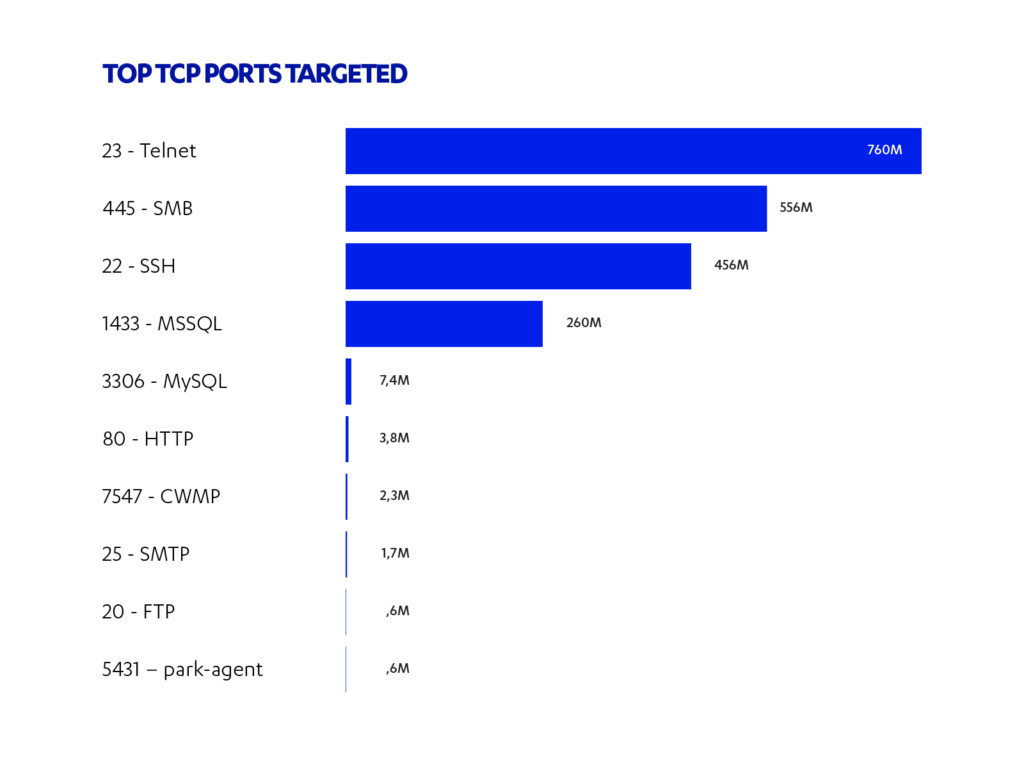
The top four TCP port targets are “23 – Telnet” with 760 million, “445 -SMB” with 556 million, “22 -SSH” with 456 million, and “1433 – MSSQL” with 260 million. The popularity of these ports isn’t random. The SMB port is related to the EternalBlue and WannaCry exploits, and as there are still a lot of unpatched systems out there, actors continue to scan. Telnet is used by IoT (Internet of Things) devices which is an exploding field in both consumer adoption and malicious targeting. The primary malware tool that is used for IoT targeting is Mirai, and as Mikko Hyppönen, CEO of F-Secure tweeted characteristically, Linux has finally gone mainstream.
Our honeypots used to see mostly Windows malware. Now they see mostly Linux malware. Linux is finally mainstream. Picture from https://t.co/HwUeX8IQ1I pic.twitter.com/PWWZoaO6cP
— @mikko (@mikko) September 12, 2019
The top source of the attacks is none other than China, with 702 million detected events. The United States follows as second, and Russia is third. This shows a sudden change in the attack landscape, as the USA occupied the top spot in H2 2018 with 306 million attacks. As for who is targeted, the top country remains the USA again, with 296 million events, followed very closely by Austria and Ukraine. Most of the attacks that originate from the US target US-based systems, while most of the attacks that stem from China target Austria, which is probably a sign of cyber-espionage.
Source: f-secure.com
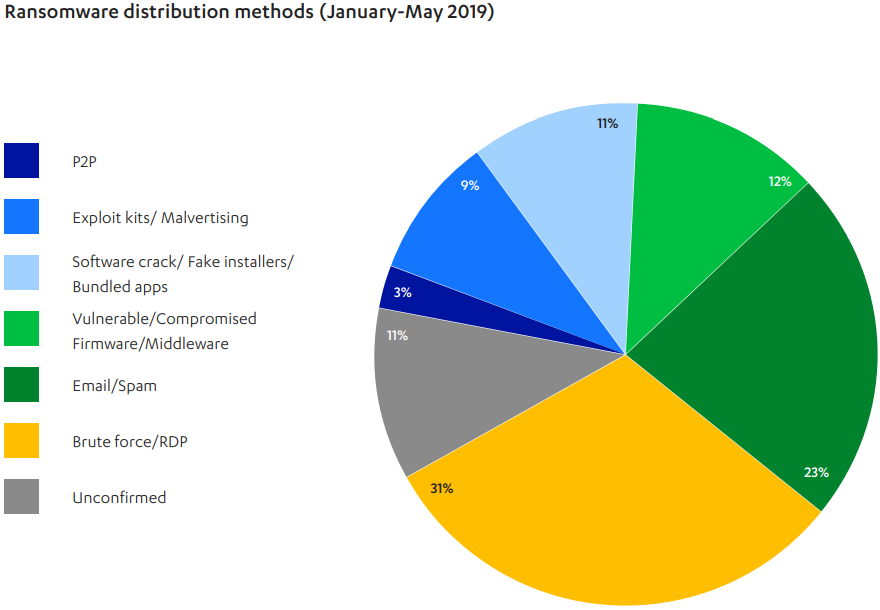
As for the ransomware trends, the most common delivery method was RDP (Remote Desktop Protocol) with 31%, followed by spam email with 23%, compromised firmware with 12%, and software crack files with 11%. The only positive observation of the report compared to what was going on in 2018 is the demise of cryptojacking campaigns that have gone extinct. Now, cryptomining only takes place as a side-effect on botnet operations, with XMRig generating Monero cryptocurrency while the malware waits for higher-level attack instructions and additional/actual payloads.
Have something to comment on the above? Feel free to share your thoughts with us in the dedicated section below, or join the discussion on our socials, on Facebook and Twitter.