
Around 20% of today's top VPN solutions are leaking the customer's IP address via a WebRTC bug known since January 2015, and which apparently some VPN providers have never heard of.
The discovery belongs to Paolo Stagno, a security researcher who goes by the pseudonym of VoidSec, and who recently audited 83 VPN apps on this old WebRTC IP leak.
Stagno says he found that 17 VPN clients were leaking the user's IP address while surfing the web via a browser.
The researcher published his results in a Google Docs spreadsheet. The audit list is incomplete because Stagno didn't have the financial resources to test all commercial VPN clients.
The researcher is now asking the community to test their own VPN clients and send him the results. For this, he set up a demo web page that users must access in their browser with their VPN client enabled. The code running on this page is also available on GitHub, if users want to test the leak locally, without exposing their IP on somebody else's server.
WebRTC leak known since 2015
Stagno's code is based on the WebRTC bug discovered in January 2015 by security researcher Daniel Roesler. Back then, Roesler found that WebRTC STUN servers, which intermediate WebRTC connections, will keep records of the user's public IP address, along with his private IP address, if the client is behind-NAT network, proxy, or VPN client.
The problem was that STUN servers would disclose this information to websites that had already negotiated an WebRTC connection with a user's browser.
Since then, many advertisers and law enforcement agencies have used this WebRTC-related bug to acquire a site's visitor's IP address.
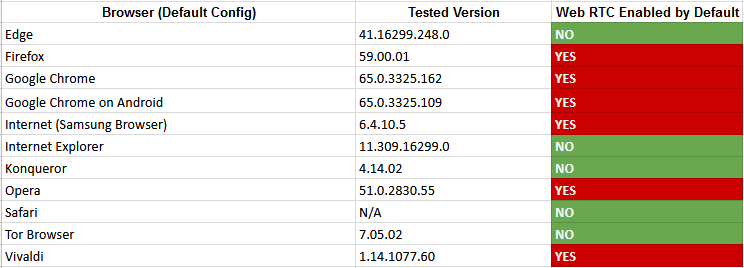
Most browsers come with WebRTC enabled by default
Browsers, who at that point spent years integrating WebRTC support in their code, rolled out features or official add-ons that would prevent the IP leak, albeit cripple some of WebRTC's real-time communications features.
Nonetheless, browsers didn't disable WebRTC, and the feature is still enabled by default in all major browsers —except the Tor Browser, Edge, and Internet Explorer.
Below is a list of VPN providers that Stagno found vulnerable to IP leaks. Around 80 commercial VPN providers remained untested at the time of writing. For updated results, please refer to Stagno's Google Docs sheet.
BolehVPN (USA Only)
ChillGlobal (Chrome and Firefox Plugin)
Glype (Depends on the configuration)
hide-me.org
Hola!VPN
Hola!VPN Chrome Extension
HTTP PROXY navigation in browsers that support Web RTC
IBVPN Browser Addon
PHP Proxy
phx.piratebayproxy.co
psiphon3 (not leaking if using L2TP/IP)
PureVPN
SmartHide Proxy (depends on config)
SOCKS Proxy on browsers with Web RTC enabled
SumRando Web Proxy
TOR as PROXY on browsers with Web RTC enabled
Windscribe Addons
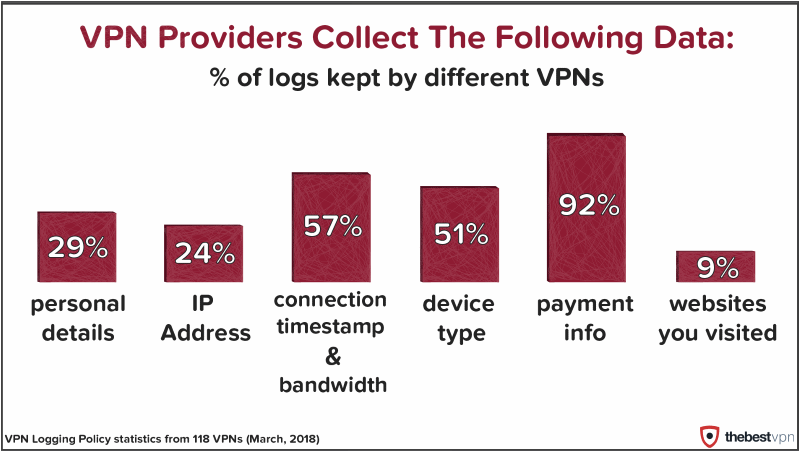
Some VPNs keep logs
And in another similarly worrisome research, the team at TheBestVPN.com also discovered that 26 out of 115 VPN clients they tested kept some types of log files.
The study didn't analyze actual VPN client installations, but privacy policies published online by each service.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now