Microsoft and Chronicle's VirusTotal have teamed up to better detect signed MSI files that have been modified to include malicious Java archives.
When a developer creates a piece of software they commonly sign them using a digital code-signing certificate to certify who created the program. Another benefit is that any modification to a signed Windows PE (.exe) will cause the signature to become invalid, which provides an extra layer of assurance that the program has not been tampered with.
While developers can also sign a Microsoft Installer (MSI) file with a certificate, it does not provide the same guarantees that the file has been tampered with. This is because it is possible to modify the contents of a signed MSI file and the signature will still remain valid.
This causes a problem as it could allow attackers to use MSI files as a storage mechanism for malicious programs and still show up as being signed. As some antivirus software rely on digital signatures to help them determine if a file is malicious, this could allow maliciously tampered files to avoid detection.
The problem with this type malware distribution method is that another program would still be required to extract the malicious code from the MSI file and execute it. This all changes if the signed MSI file has a malicious Java JAR file appended to it according to a new blog post by VirusTotal..
Zip files are read from the end of the file
Java Archives (JAR) files are simply Zip files containing the necessary components, code, and manifests that allow them to be executed by a Java launcher. According to the Zip file specification, a valid Zip archive ends with a "end of central directory record" that indicates the end of the ZIP file and optionally contains file headers for each file stored in the archive.

VirusTotal explains that as JAR files are simply Zip files, when Java executes one it does so by reading from the end of the file to the beginning of the archive and ignore the rest of the MSI file. This allows attackers to distribute signed MSI files with appended malicious JAR files, rename them to a JAR file, and then execute them using Java's javaw.exe launcher.
"The interesting part for exploiting the commented scenario is the JAR file format is based on ZIP to store the different components and resources, and this kind of ZIP is correctly identified by the presence of an end of central directory record which is located at the end of the archive to allow the easy appending of new files. When Java opens a JAR file it looks at the end instead of the beginning of the file, so a JAR file is executed independently of the data at the beginning of the file. In addition, on Microsoft Windows systems, the Java Runtime Environment's installation program will register a default association for JAR files so that double-clicking a JAR file on the desktop will automatically run it with "javaw -jar". "
To illustrate this type of malicious MSI file, VirusTotal provided a sample discovered in the wild that was utilizing the above method. Chronicle told BleepingComputer via email that vendors on VirusTotal are detecting these types of samples as "Jacksbot" and that they are extremely rare.
"This technique has proven, so far, to be extremely rare," Chronicle told BleepingComputer. "While you can append anything to the end of an MSI, in this particular case, only a JAR would execute in the manner described by the original blog post."
VirusTotal teams up with Microsoft
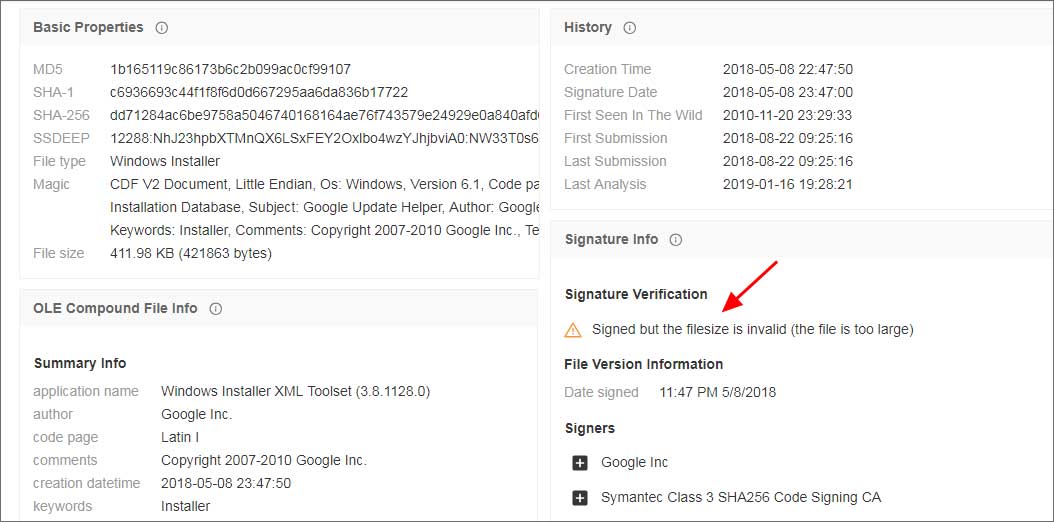
Working with Microsoft's Mark Russinovich and Mark Cook, Microsoft updated their Sigcheck tool to indicate if a signed MSI has been tampered with. This new detection can be found in Sigcheck 2.70 and is being used by VirusTotal to detect modified signed MSI files when they are uploaded to their service.
If Sigcheck detects a modified signed MSI file it will now display the warning "Signed but the filesize is invalid (the file is too large)" as shown below.
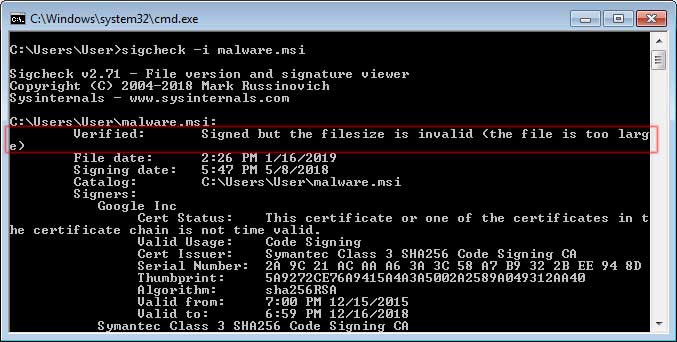
This new detection is also displayed in the command line out as shown below.
The Microsoft Security Response Center also took a look at these types of malicious files and stated that they show as signed in the latest and updated versions of Windows 10 and Java. Microsoft has decided not to fix this issue in the current versions of Windows at this time.
"This attack vector has been verified in the latest and updated versions of Windows 10 and Java available at the timing of writing (Windows 10 Version 1809 and Java SE Runtime Environment 8 Update 191). Microsoft has decided that it will not be fixing this issue in the current versions of Windows and agreed we are able to blog about this case and our findings publicly."



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now