IDS/IPS with NSX-T
VMware has announced a new NSX-T Version 3.0 on 7th of April 2020. This version is a major release with many new features. VMware added several new function in the areas Intrinsic Security, Operations, Multisite (Federation), Containers, Load Balancing Enhancements, VPN Enhancements, Routing, Automation and Cloud connectivity. I want to take a closer look within this blog post to the Intrusion Detection System/Intrusion Prevention System (IDS/IPS) feature.
Most companies are using IDS for the east-west security inside the data centre and IPS for the north-south security. For the release NSX-T 3.0 IDS is available, IPS will be provided with future releases.
What is a IDS/IPS system?
IDS/IPS systems can be implemented in hardware or software. IDS/IPS system protection is against vulnerabilities exploits which can be done as malicious attack to a application or service. Attackers use this to interrupt and gain control of the application. IDS/IPS technology rely on signatures to detect attempts at exploiting vulnerabilities into the applications. This signatures are comparable to regular expressions which compare network traffic with malicious traffic patterns.
IDS (Intrusion Detection System) is like the name already says an monitoring system and IPS (Intrusion Prevention System) is a control system which blocks the traffic in case a attack is detected. This means with IPS you have the risk of false positives.
How IDS runs with NSX?
As already mentioned with NSX-T 3.0 release VMware announced IDS (Intrusion Detection System) with NSX-T 3.0. IPS function will be provided in the next months.
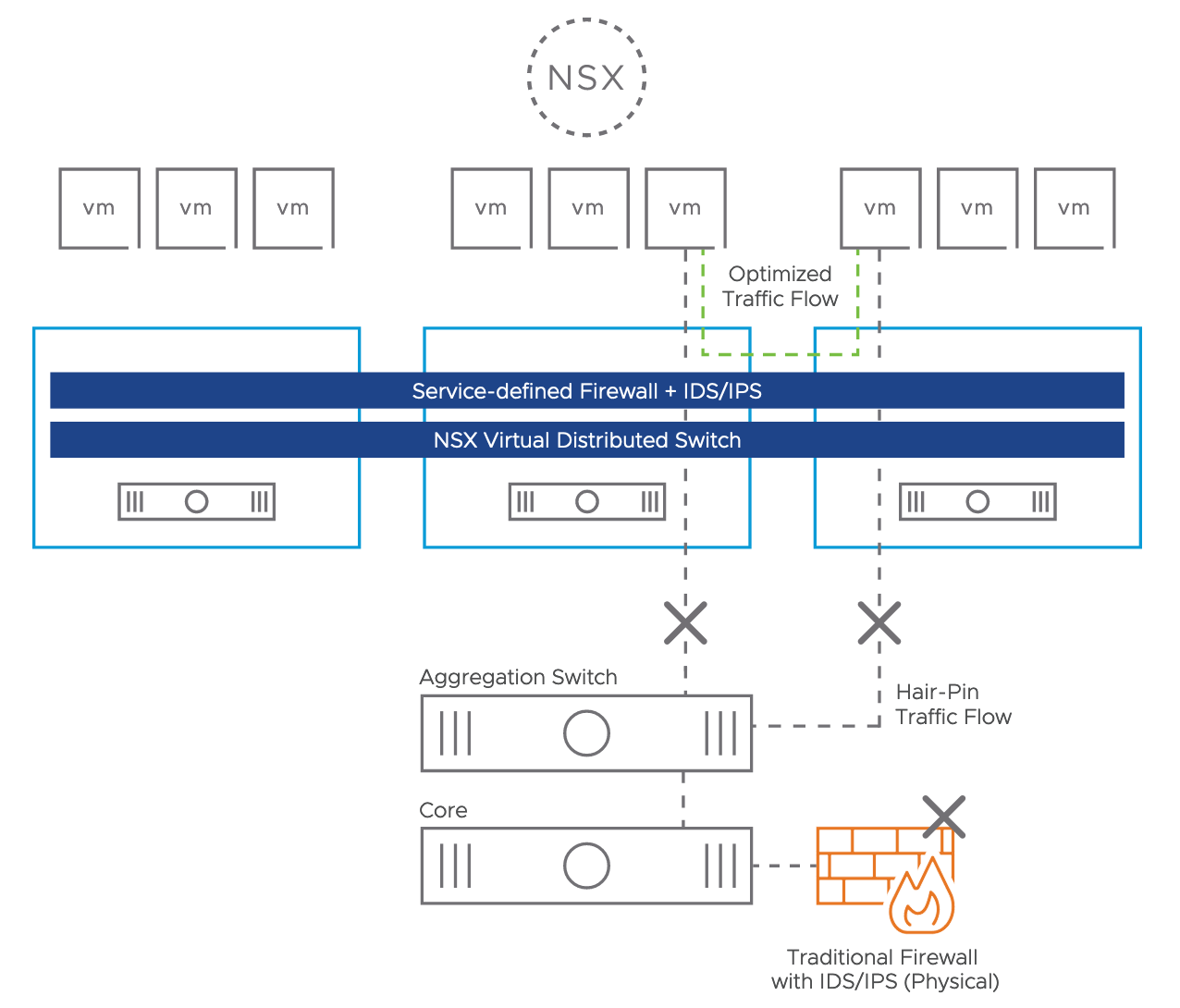
IDS is hypervisor based and is sitting in front of the vNIC on the ESXi host (see picture 1). The design is based on the NSX DFW (Distributed Firewall) concept. No agent is necessary, the communication is realized via VMware tools. A VMware VIB (vSphere Installation Bundle) will be rolled out for the host preparation. With this technic you avoid hair-pin because instead of traditional firewall with IPS/IDS the function is covered directly on the host level without any dependency to the network or any IP address ranges.
The signatures will be provided from the cloud service provider Trustwave directly to the NSX Manager. For this purpose the NSX Manager needs internet access, offline downloads are also supported. The signature updates could be provided immediately, daily or bi-weekly.
Picture 1: IDS System Hypervisor based
What are the use cases for IDS with NSX?
DMZ (Demilitarized Zone)
NSX IDS has the possibility to establish a DMZ (Demilitarized Zone) in software. One approach could be to realize this completely on the virtualization level or another choice could be to use dedicated ESXi Hosts for the DMZ. The NSX Distributed Firewall (DFW) and the Distributed IDS allow customers to run workloads centralized for different tenants.
Detecting Lateral Threat Movement
Usually the initial attack is not the actual objective, the attackers try to move through the environment to reach the real target. The NSX Distributed Firewall (DFW) with Layer-7 App-ID features helps there a lot that the attacker could not exploit the attack. For example the ransomware attack “WannaCry” is based on port 445 and 139 with SMB and could not be avoided with NSX DFW. With IDS technology the attack could be detected and would not be moved to other machines.
Replace physical IDS Systems
Another use case could be to remove the physical firewalls or IDS systems and replace it with NSX.
Meet regulatory compliance
Many data centre workloads have Intrusion Detection System (IDS) requirements for regulatory compliance, i.e. sensitive Health Insurance Portability and Accountability Act (HIPAA) for healthcare, and the Payment Card Industry Data Security Standard (PCI DSS) or the Sarbanes-Oxley Act (SOX) for finance.
How does IDS work with NSX?
The installation effort and the operational overhead is low when NSX is already implemented. There are only a few steps necessary to get the IDS function up and running.
1. Configure IDS Settings
The NSX-T Manager needs internet access to download the signatures, it could be done with auto-updates or manuel. It is also possible to define an Internet Proxy (HTTP/HTTPS). The VIB (VMware Installation Bundle) rollout can be realized via cluster or standalone ESXi Host (see picture 2).
Picture 2: Configure IDS Settings
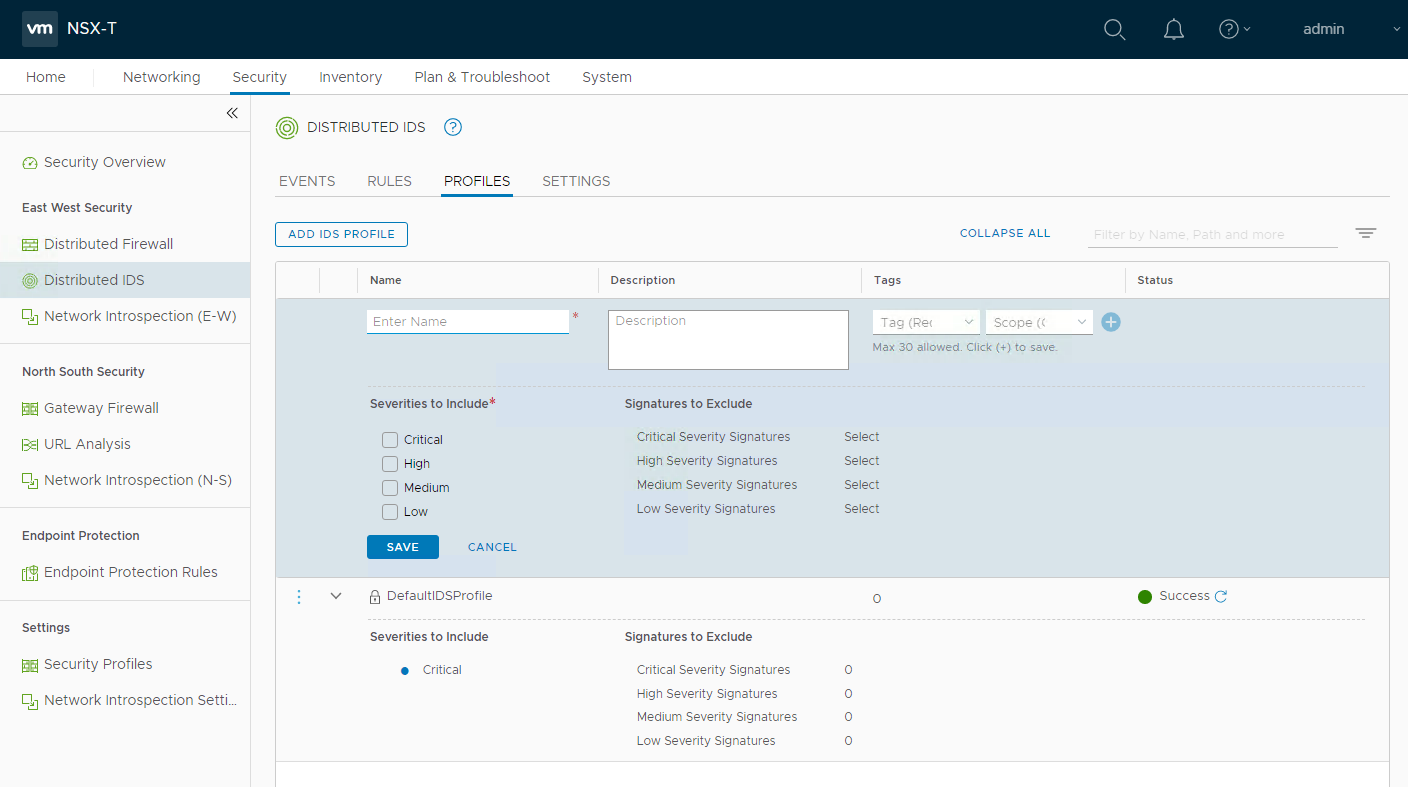
2. Configure IDS Profile
The second step would be to configure an IDS Profile if you do not want to use the default profile (see picture 3). During this step Severities can be defined from Critical, High, Medium to Low which are based on CVSS (Common Vulnerability Scoring System) score.
Picture 3: Configure IDS Profile
3. Configure IDS Rules
The last IDS configuration step will be to create an policy with IDS rules (see picture 4). The administration of IDS rules are very similar to the DFW firewall rules. A configuration of a IDS rules includes name, sources, destinations, services, IDS profile and the applied to field.
Picture 4: Configure IDS rules
4. Monitor IDS Events
When IDS is configured the events can be monitored over the dashboard which is visible below in picture 5.
Picture 5: Monitor IDS events
Summary
IDS (Intrusion Detection System) is another major step for NSX within the Intrinsic Security area. IDS in software, Distributed & Built-in Analysis, no hair-pinning traffic, meet regulatory compliance, fits DMZ requirements, no lateral thread movement and simple operations are all arguments to validate this new feature.