A PayPal phishing campaign is luring victims to a hacked site where a clone of the PayPal login page is trying to trick users into giving away their PayPal credentials, payment card details, and ... a selfie of the user holding his ID card.
Brought to Bleeping Computer's attention by security researchers from PhishMe, the crook behind this operation relies on spam emails to drive users toward a PayPal phishing page hosted on a compromised WordPress site from New Zealand.
At the time of writing, the phishing page had been removed, but following a classic pattern for phishing sites, users arriving on this page were asked to log in with their PayPal credentials.
There was no attempt to spoof the browser URL, so if users had any kind of experience with phishing pages, they would have immediately noticed they were on a page with the wrong address.
Greedy crook wants more data
Once users entered their logins, the crook wasn't satisfied. At this point, it was obvious he's dealing with an inattentive or untrained user, so this phisher decides to go all-in and ask for more data. During a four-step process, the attack asks for the user's address, payment card data, and a picture of the user holding his ID card.
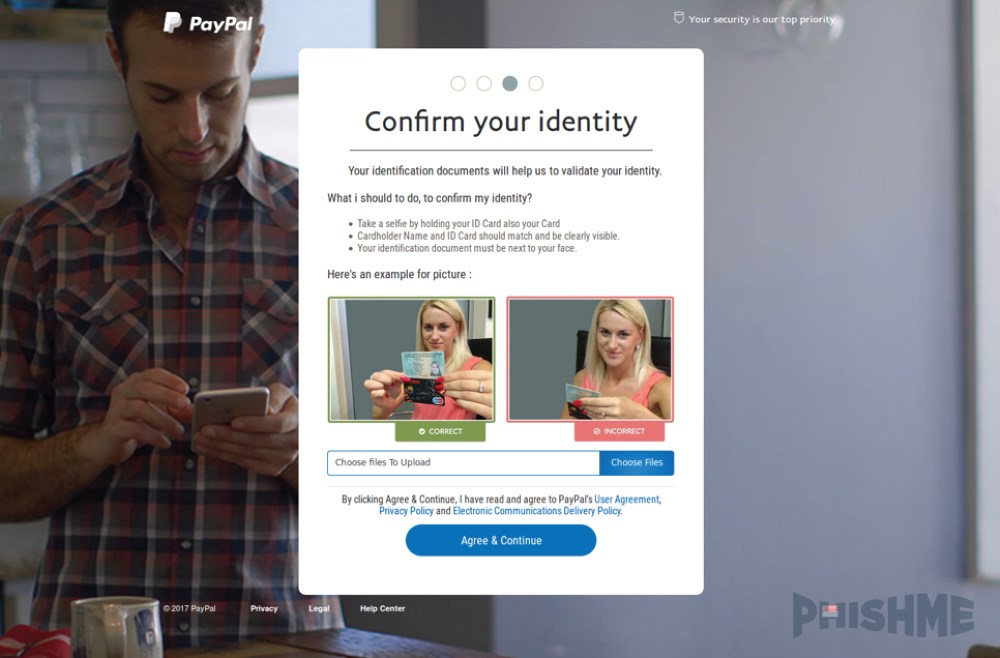
It is unclear why the crook would ask for this information. PhishMe expert Chris Sims believes it is "to create cryptocurrency accounts to launder money stolen from victims."
A similar tactic was seen last year
This tactic of asking a user for a selfie while holding his ID card has been seen before. In October 2016, McAfee discovered a variant of the Acecard Android banking trojan that was also asking users to take a selfie holding their ID card when logging into their mobile banking accounts.
The tactic was quite innovative at the time, and it got a lot of press coverage. It may be plausible that the author of this phishing scam might have come across it and decided to adapt it for his phishing operation.
The way the "selfie upload" procedure has been implemented is also curious. Instead of relying on WebRTC or Flash to access the user's webcam to take a photo and save it automatically in the form, the crook asks users to upload a photo from their computer. This means more hassle, as the user has to take a selfie, transfer it to the PC, and then upload it on the crook's page. Prolonging the attack this way gives the user more time to notice something wrong with the fake PayPal site.
In addition, there's a second issue. Phishing sites usually don't feature form validation rules, taking whatever users enter in the forms. This phisher broke out of this mold and wrote special form validation rules to make sure the user is uploading the photo in JPEG, JPG, or PNG format.
The crook also made mistakes. The user's photo isn't saved to a server under the crook's control, but sent to an email address at "oxigene[.]007@yandex[.]com."
Sims says he searched for this address in the Skype user directory and found it registered to a person named "najat zou," from "mansac, France." While this information is not reliable to determine the user's nationality or location, it provides researchers with a first clue they can use to track down the phisher if law enforcement decides to investigate this case further.
Image credit: PhishMe


Comments
archer667 - 6 years ago
I hope no one fell for this scam. But just saying, both the user and the attacker can also be "she", not necessarily "he" (even in the phisher's picture)!
King_Yoshi - 6 years ago
The pictures with the ids can be used for stealing peoples identity.
You can use these pictures to "verify" your identity with paypal and steal their account.
campuscodi - 6 years ago
PayPal doesn't ask you for a photo with your ID. They usually ask for high-resolution scans.
JesseBropez - 6 years ago
I think they do accept photos...as long as the photos are high quality.
GoofProg - 6 years ago
I remember a porn series that used to hold up their driver's license to the camera. The theme is the men were about 40 years old and the women were 20 years old. So they would should their IDs or passports to the camera to show how old they were to prove they were legal because they were shagging with people half their age as a fetish play.
Nillaice - 5 years ago
I have just been a stupid victim. I thought it was a silly request but figured maybe they need to prove I am who I say I am on my I.d. any way my bank has contacted me and blocked my card as it had suspicious activity in Nigeria manufacturer topuo and earn. I can no longer access the site through my history and wonder what else they can have with my information